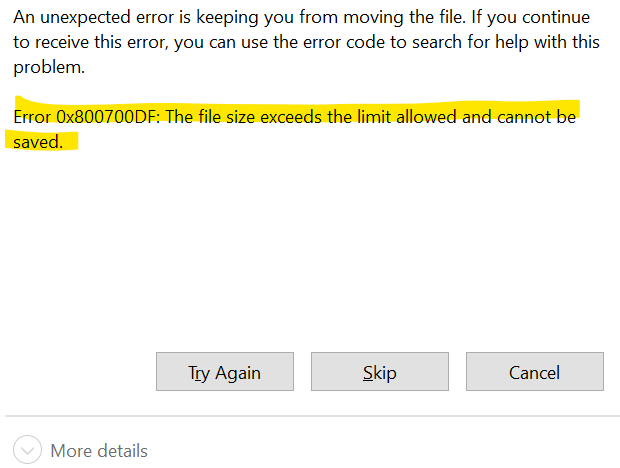
- Decrypt Old Vault App Filesystem
- Decrypt Old Vault App Files Windows 10
- Decrypt Old Vault App Files Windows 10
- Decrypt Old Vault App Files Free
With the constantly increasing of modern people’s awareness of privacy protection, data/file encryption has become an indispensable part of our lives. Especially for some large companies and high-ranking workers in the office, looking for a good and practical file encryption software for computer is not so easy because the file encryption software market is flooded with innumerable similar encryption products from which you can hardly determine which to use.
On dropbox.com—Click the padlock icon in the top-left corner of your vault. On the Dropbox mobile app—Tap “ ” (ellipsis) in your vault, and then tap Lock Vault. In File Explorer (Windows) or Finder (Mac)—Right-click your vault and click Lock Vault. Your vault’s security measures are in addition to the security measures Dropbox. If you're an Android user, follow these steps to restore photos and/or videos from Vault to your device: Open the Vault app. Tap Photos or Videos. Tap the Menu button on your phone then tap Manage Photos or Manage Videos. Find the Photo (s) or Video (s) that you'd like to restore and tap to select.
Moreover, for the safety of vital files, they usually require a higher level of security for encryption, and the required file encryption software is mainly for business, not the general personal using. But don’t worry for we have sorted out the top 12 best file encryption software for you in this article, which can save your time and energy of finding out the most suitable file encryption software for Windows and Mac computer. The following is a general introduction and review on these 12 free file encryption software.
1. Gihosoft File Encryption (Windows)
Gihosoft File Encryption is one of the best file encryption software for PC. With which you can lock files and folder, create virtual disk to password protect files, make dummy files to confuse others, upload files to cloud. As a practical file encryption software for Windows, it mainly adopts the password to protect your vital or sensitive data/files, so only those who know the correct master password can open this program to access relevant data/files.
With a clean and intuitive graphic user interface, this program can let you conveniently find the function you need exactly, making it easy for you to get started! It both supports folder encryption and multiple file type encryption, such as the Excel file, picture file, Word file, etc. Besides, you can also create a virtual disk in which you can put files/folders to achieve file/folder encryption as well. It’s worth mentioning that you can download this file encryption software to try before purchase.
2. VeraCrypt (Windows/OS X/Linux)
VeraCrypt is another practical file encryption software which is free for users to download on Windows, OS X, and Linux. VeraCrypt is the branch and successor of TrueCrypt. It usually uses AES to encrypt files, in addition to TwoFish and Serpent. Apart from the encryption for individual folders of files, VeraCrypt can also create a virtual encrypted disk in a file, or use a pre-boot authentication to encrypt the partition or (in Windows) the entire storage device.
Those who love VeraCrypt praise it as an instant encryption tool because your files are only decrypted when needed and are encrypted at all other time. At the same time, many people say that even if it lacks a good-looking interface, it is still a powerful tool that is easy to use. You also noticed that VeraCrypt may not support TrueCrypt files and containers, but can convert them to its own format. Its development team is constantly working hard to improve the user experience, making it more functional.
3. 7-Zip (Windows/OS X/Linux)
7-Zip is a free file archiving program that is used to place files in a compressed container called “archive”. But in addition to that, it is still a good file encryption software for computer. It is mainly compatible with Windows, OS X, and Linux systems. It is worth noting that the official download of this file encryption software only supports Windows systems, but there are also unofficial versions supporting Linux and OS X systems.
7-Zip can convert a single file or an entire volume into an encrypted volume that only has the key you own. This program is completely free, even for commercial use, and it also supports 256-bit AES encryption. In addition to the security key, the single file can also be encrypted with a password and converted to an executable file that will be self-decrypted when it reaches the intended recipient.
4. AxCrypt (Windows)
AxCrypt is also an excellent free file encryption software for Windows 10/8/7 we strongly recommend for you. As a free, open source, and GNU GPL licensed encryption software, it is proud of its simplicity, efficiency, and ease of use. It integrates well with the Windows shell, so you can right-click on the file to encrypt it.
The best part is that it provides “timed” executable encryption to automatically decrypt the file after a certain period of time, or to automatically decrypt it when its intended recipient receives it. Files encrypted with AxCrypt can be decrypted as needed or kept decrypted while in use and then automatically re-encrypted when modified or closed. AxCrypt runs very fast, although you can choose to encrypt the entire folder or a large set of files.
5. BitLocker (Windows)
As we all know, BitLocker is a complete volume encryption tool which is built into Windows systems, and it supports all Windows versions starting with Windows Vista. In other words, it achieves data protection primarily by providing encryption for the entire volume. By default, it uses the AES encryption algorithm in the Cipher Block Chaining (CBC) or the XTS mode with a 128-bit or 256-bit key.
It provides users with a variety of authentication mechanisms, and the common ones of them are the traditional password and USB “key”. In addition to these two mechanisms, the controversial Trusted Platform Module (TPM) technology (using hardware to integrate keys into devices) is also used. Either way, the integration of BitLocker with Windows (especially Windows 8 Pro) makes BitLocker accessible to many people. At the same time, BitLocker is a viable disk encryption tool, especially for individual users who need to protect data when a laptop or hard drive is lost or stolen, in case their data is maliciously compromised.
6. LastPass
LastPass is probably the most important choice as the best password manager tool for users. All the incredible features which this password manager tool offers are beneficial and handy for the users. The best part of using this password manager tool is that it is safe and secure than most of the other password manager tools available for the users. The latest encryption technology used in this password manager tool is pretty much capable of delivering high-end results to the users as their saved passwords will never get exposed or hacked suspiciously by the users. The easy to use and intuitive interface of this password manager tool is another very bad thing for the users, which attracts them the most. There is also a user-manual guide available for the users which they can read to set up as secure and safe password onto their accounts and other related websites. The two-factor authentication system available in this password manager tool is another considerable advantage for the users, which will add an extra layer of security in their accounts. Moreover, users can save or store different passwords for the multiple accounts present in their devices.
The advanced and optimized techniques of this password manager tool are probably the best part of it. When the features are optimized, then you will experience high-quality security features. The mobile application of LastPass is available for both Android and iOS users. Furthermore, users can also use the extension of the LastPass password manager tool in their main web browsers like Google Chrome, Mozilla Firefox, etc. So, LastPass is an excellent choice for users with a lot of optimized features.
7. FileVault2
This password manager tool is designed and developed for macOS and Mac Hardware. FileVault2 software tool is an excellent choice for users who want to block every single unauthorized access into their private accounts. This password manager tool will not only manage your passwords but also it will provide you the security and privacy protection as well. FileVault2 password manager tool is developed with secured AES-128 encryption along with a crucial 256-bit algorithm to secure the passwords which have been saved by the users in their Mac devices. This password manager tool is an open-source software tool that can be used by any Mac user. However, this software also comes in a paid version, which will unlock premium security features to manage the passwords saved in the devices. The overall graphic user-interface of this software is also developed pretty much enhanced by its developers to make it more attractive than other software tools. There is no single chance for hackers to penetrate the security breaches set up by this password manager tool. All the passwords which have been saved in this software tool are entirely safe and secured. There is nothing to worry about when you have used FileVault2 encryption software on your device to secure your passwords and other confidential data.
8. DiskCryptor
Yet another very excellent choice for the users as a free, open-source, and encryption software. As the name of this software itself suggest that this software can be used to encrypt or secure the data present in the internal or external hard disks of your PC. Even the system partitions and ISO images can be encrypted using this brilliant software whose name is DiskCryptor. The easy to use interface of this software is awesome, which will let you operate this software hassle-free. DiskCryptor is a full disk encryption tool that is now made as a partial disk encryption tool. There are multiple encryption techniques or algorithms that are working behind the functionality of this software like AES encryption, Twofish encryption, and many more secure encryption techniques as well. All you need to do is click on the “Encrypt data” option available inside this software and select the parts of the disk which you want to encrypt. After selecting the files, proceed to further guidelines to accomplish your task of encryption. As we already mentioned, DiskCryptor is very easy to use for every user, and encrypted data is safe and secured with this software. Users are not required to register themselves on this software as it doesn’t require any registration process to be done for the setup. Just launch this software on your PC, followed by a selection of files to encrypt them will do the job for you. We highly recommend this software to our users as DiskCryptor is very easy to use, and the interface of this software is incredibly well developed.
9.HTTPS Everywhere
Decrypt Old Vault App Filesystem
HTTPS Everywhere is a web browser which is particularly developed for the users who want to experience secured surfing on the web. Because data privacy is still the most critical concern among the users, hence HTTPS Everywhere browser becomes a good option to surf safely on the internet. The HTTPS Everywhere can be used in your system with other web browsers like Google Chrome, Mozilla Firefox, etc. as well. The encryption technology used by this web browser is pretty much optimized and latest, which will make sure that your private data will not get hacked in any case.
Because most of the bank frauds and other financial frauds are done online, that’s why there is an urgent need for software that can protect the users from online fraud. And HTTPS Everywhere software is doing the same job for the users. This encryption software is pretty much secured, and there are no chances that anyone can steal any single bit of data from your systems. So, we would suggest our users install this browser on their PC for a safe and secure internet surfing.
10. Tor Browser
Tor Browser is yet another perfect kind of web browser which is developed to secure the traces of your online activities. This browser will secure all your online activities from prying eyes of hackers and other wrongdoers. The most important thing related to this software is that Tor browser will never let the hackers steal the IP address of your PC. The tor browser will always mask your identity in front of all users and will never let your privacy to be exposed. The latest version of Tor Browser 0.4.0.4 comes with several bugs fixes which makes it more convenient and relevant for the users. The latest and newly optimized alpha version of the tor browser is going to release very soon, which will offer so many newly optimized features to the users.
11.CyberGhost
Basically, CyberGhost is not typical encryption software. CyberGhost is a VPN that users can use to connect to different networks and can make sure that their private data will remain confidential. VPN connections are the most secured connections available on the web, which are pretty much efficient as well. And one name in the segment of popular VPN connections is CyberGhost, which is an outstanding choice for the users. CyberGhost is developed with the latest encryption algorithms by the developers who can protect your online identity and data from suspicious activities. CyberGhost provides the feature of connecting to more than 100 different web servers of more than 50 plus countries. As browsing in private mode will secure your privacy concerns, that’s why CyberGhost becomes an excellent choice for every user. CyberGhost has recently won the “Best Value” category award of top VPN awards 2019.
CyberGhost VPN also offers a 30-day money-back guarantee to the users. Furthermore, CyberGhost works very well with almost every OS like Windows, iOS, Mac OS, and Android OS as well. The basis user-manual guide available on this software is also beneficial for the users who are using a VPN connection for the very first time. That manual will guide them on how to use a VPN and how to switch the server connections instantly. That’s why to secure and encrypt all your digital assets in the most efficient manner; there will be no other choice better than CyberGhost VPN.
12. ExpressVPN
Another trendy name in this section of top VPN companies is ExpressVPN, and this undoubtedly one of the most incredible options which we have ever seen. The latest 256-bit AES encryption technology algorithm is used in this VPN connection, which is having on the most advanced privacy protection features. Express VPN also offers almost the same kind of functions as provided by CyberGhost VPN. ExpressVPN offers a 30-day money-back guarantee to its users, which is probably one of the best features of this software. You can easily connect your PC to the servers of almost 148+ locations of 90 different countries, which is an incredible feature. Talking about the compatibility of ExpressVPN, then it is pretty much compatible with Windows, Android, iOS, and Mac OS as well. That’s why ExpressVPN has a huge fan following, and there can be no option better than this VPN company. The graphic user-interface of this VPN is also a great thing about it. Moreover, ExpressVPN is very simple and easy to install and use. The overall setup is also very convenient and reliable to use. So, ExpressVPN should be your backup choice because most of the VPN like CyberGhost is recently launched, and they frequently go out from working. So, in that case, ExpressVPN should have to do the job for you.
Applying these security measures to enhance your online safety

In this part of the article, we will now discuss some basic set of different security layers. There are many things which should be kept in mind while setting up multiple layers of security, such as:
- Using Antivirus software: If we use antivirus software on our PC, then it will provide an extra layer of protection from hackers. Additionally, antivirus software will also offer some different functions to use as well. However, you have to spend some additional money to purchase premium Antivirus software. Antivirus software will make sure that you are getting all-around protection for all your digital assets.
- Keeping both browser and OS up to date: Another very crucial thing which we should keep in our mind while setting up multiple layers of security is that we should keep both the OS and the web browser of our system updated.
- Be careful while connecting to Public networks: It is a well-known fact that the majority of the privacy threat is given by the public networks which aim to steal the confidential data of the users.
Conclusion:
Those listed above are the top 12 best file encryption software that we have carefully selected for you from a wide range of similar products. We hope that you will consider them practical, and you can share these 12 best free file encryption software with your friends and family members who may be in need now. If you need help, you can leave your message in our comment section below!
Related Articles
Please enable JavaScript to view the comments powered by Disqus.One of the things we recently hit was authentication cookies and password reset tokens getting invalidated in an Azure App Service. The app uses deployment slots to deploy the new version there before swapping it to production. So what's common between authentication cookies and Identity password reset tokens in ASP.NET Core?
They both use Data Protection to encrypt their content. So what seemed to be happening is that those cookies/tokens were no longer accepted. The protection keys had changed.
What the issue is and why it happens
Let's start with a quote from the documentation on default settings for Data Protection:
If the app is hosted in Azure Apps, keys are persisted to the %HOME%ASP.NETDataProtection-Keys folder. This folder is backed by network storage and is synchronized across all machines hosting the app.
Keys aren't protected at rest.
The DataProtection-Keys folder supplies the key ring to all instances of an app in a single deployment slot.
Separate deployment slots, such as Staging and Production, don't share a key ring.
When you swap between deployment slots, for example swapping Staging to Production or using A/B testing, any app using Data Protection won't be able to decrypt stored data using the key ring inside the previous slot. This leads to users being logged out of an app that uses the standard ASP.NET Core cookie authentication, as it uses Data Protection to protect its cookies. If you desire slot-independent key rings, use an external key ring provider, such as Azure Blob Storage, Azure Key Vault, a SQL store, or Redis cache.
That last bit is the critical one. This is what happens:
- Version 1 of app published to production
- Data protection keys created and stored on the file system
- A user signs in, cookie created, encrypted with data protection keys
- Version 2 of app deployed to staging deployment slot
- Staging swapped to production
- The original data protection keys swapped to staging since they are in the file system
- New data protection keys generated and stored in production file system
- Version 2 app gets a request with the cookie
- Decrypting the cookie with data protection keys fails, data is invalid
- Authentication fails :(
Getting the keys out of the file system
To solve the issue, we need to get the data protection keys out of the file system. The keys are persisted to an XML file. So Azure Blob Storage works pretty well for that.
But the keys aren't encrypted by default. So anyone with access to the Storage account could access the keys used to secure authentication cookies etc. Not great.
And that's why we will additionally encrypt the keys using keys in Azure Key Vault.
Note that we mainly need to do this while running in Azure. This isn't usually necessary for local development.
Persisting keys to Azure Blob Storage
The first step we will take is to configure the keys to be stored in an Azure Storage account. So you'll need one of those if you're following along.
Now there are built-in functions to add Azure Blob Storage persistence for Data Protection, but none of those allowed for what we want. Namely we want to specify the blob reference factory passed to the AzureBlobXmlRepository instance. We want to use the Azure App Authentication library to leverage Managed Identities in Azure, and to leverage the developer's user account while developing locally (if you decide to do this while running locally as well).
Here is what we added in ConfigureServices of the Startup class:
The AzureServiceTokenProvider object is setup in the constructor:
It's not very nice that the infrastructure for Data Protection is synchronous. Honestly it makes very little sense considering basically all key storage methods are asynchronous by nature.
Anyway, this is what the code does:
- Gets a strongly-typed object of configuration settings (you'll see what those look like in a bit)
- Adds services for Data Protection (so we can add Key Vault encryption to it in the next step)
- Configures the repository to use for storing keys
- This is exactly what
PersistKeysToAzureBlobStorage()would do if you called that on the object returned byAddDataProtection()
- This is exactly what
- In the function we:
- Get an Azure AD access token Storage through the Azure Service Authentication library
- Note the user / service principal must have Blob Data Contributor role at the storage account level, for some reason setting it to container level did not work :/
- Builds a blob reference with the token and all the coordinates to locate the blob
- Get an Azure AD access token Storage through the Azure Service Authentication library
Here is how the configuration looks like:
And the corresponding settings class:
The Azure AD tenant id is needed only for local development. If you don't need it, you can remove the setting and remove its usage and leave the tenant id null.
With this in place, the keys would now be stored outside the app and everything would work great :)
Except for one little thing, the keys are not encrypted in Storage :(
Encrypting the encryption keys in Storage
To offer an additional layer of protection, we can encrypt the keys stored in Blob Storage using a key in Azure Key Vault. Setting it up is really easy.
First you'll of course need an Azure Key Vault. Then you can create a key in the vault.
Here's how you create a key:
- Open the Key Vault blade
- Go to Keys
- Click Generate/Import
- Give it a name
- Choose key type and key size
- Click Create
After creating, open the key and open the current version. You'll have the option to copy the key identifier, do that.
Add the key id to the config:
And add a corresponding property to the settings class:
Then you'll need to create an access policy to allow the users/service principals to wrap and unwrap keys in the Key Vault.
Then we can quite easily add the Key Vault protection:
And that's it. The keys file will now be encrypted/decrypted using the key in Key Vault. The key itself will never be in the app's memory.

Okay, we may have slightly over-simplified when saying the file is encrypted by Key Vault. What actually happens is that an AES key is generated to encrypt the XML file. The XML text is encrypted with the key. The key is then 'wrapped' by using the Key Vault key. This wrapped key (i.e. encrypted key) is then stored alongside the encrypted data in Storage.
Then to decrypt the data, the wrapped key is unwrapped using Key Vault. Then that key is used to decrypt the data.
What this means is that the key in Key Vault is never in your app, and the Data Protection keys will never go to Key Vault. This is quite a good solution since it'll scale really well. Even if you had a ton of keys stored in the XML file, only the main generated encryption key needs to be wrapped/unwrapped with Key Vault.
You can see how the decryption works in the source code.
Final results
The libraries we have in the ASP.NET Core 2.1 app:

- Microsoft.AspNetCore.App (no version specified)
- Microsoft.AspNetCore.DataProtection.AzureKeyVault (2.1.1)
- Microsoft.AspNetCore.DataProtection.AzureStorage (2.1.1)
- Microsoft.AspNetCore.Razor.Design (2.1.2)
- Microsoft.Azure.Services.AppAuthentication (1.2.0-preview2)
- WindowsAzure.Storage (9.3.3)
Decrypt Old Vault App Files Windows 10
The configuration:
The AAD tenant id is only needed for local development, though there is no harm in specifying it otherwise.
Decrypt Old Vault App Files Windows 10
Note every environment should use its own key file. So you'll want to make sure that the blob name/location is overridden in every environment.
The settings class corresponding to the config:
Configuration in the Startup class:
Some test code to see it all works:
And the corresponding view:
With this test code we can confirm that the cookie value is successfully decrypted even after deploying a new version to a deployment slot and swapping that to production.
Summary
After configuring Azure Storage persistence and Key Vault protection, we now have a nice solution that works across deployment slot swaps. It also uses exactly zero credentials stored in the app to talk to both Azure Storage and Azure Key Vault.
Hope this is useful, until next time :)
Links
Decrypt Old Vault App Files Free
- Official docs, protecting keys with Key Vault https://docs.microsoft.com/en-us/aspnet/core/security/data-protection/configuration/overview?view=aspnetcore-2.2#protectkeyswithazurekeyvault
- Official Data Protection docs https://docs.microsoft.com/en-us/aspnet/core/security/data-protection/introduction?view=aspnetcore-2.2